问题如题:
其中参照了
https://www.jianshu.com/p/54646ac96473
https://blog.csdn.net/yelllowcong/article/details/79238335
并根据教程做了如下配置:
1、修改service文件,HTTPSandIMAPS-10000001.json
{
"@class" : "org.apereo.cas.services.RegexRegisteredService",
"serviceId" : "^(http|https|imaps)://.*",
"name" : "HTTPS and IMAPS",
"id" : 10000001,
"description" : "This service definition authorizes all application urls that support HTTPS and IMAPS protocols.",
"evaluationOrder" : 10000,
"attributeReleasePolicy" : {
"@class" : "org.apereo.cas.services.ReturnAllAttributeReleasePolicy"
}
}
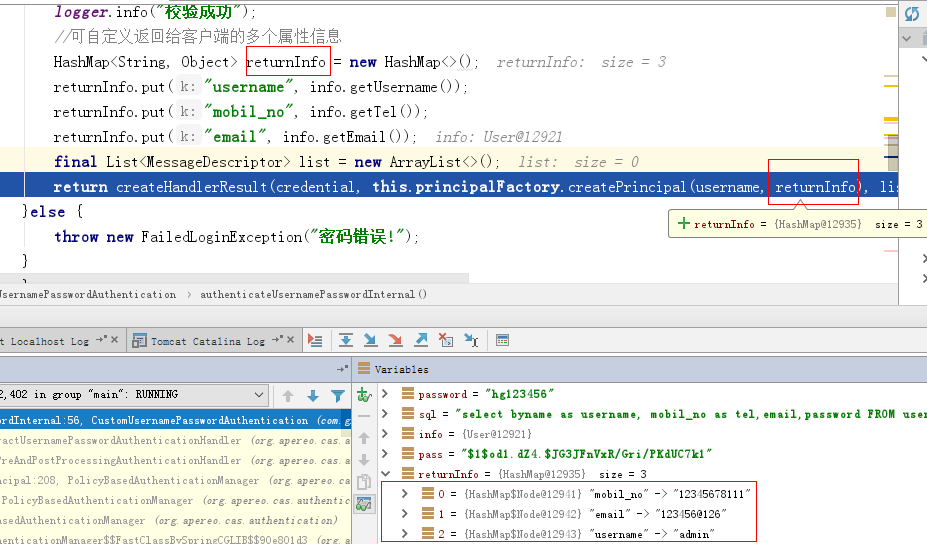
2、自定义验证以及返回更多的个人信息
3、spring.factories文件配上自己自定义的流程,其他的去掉
org.springframework.boot.autoconfigure.EnableAutoConfiguration=com.gxzytech.config.CustomAuthenticationConfiguration
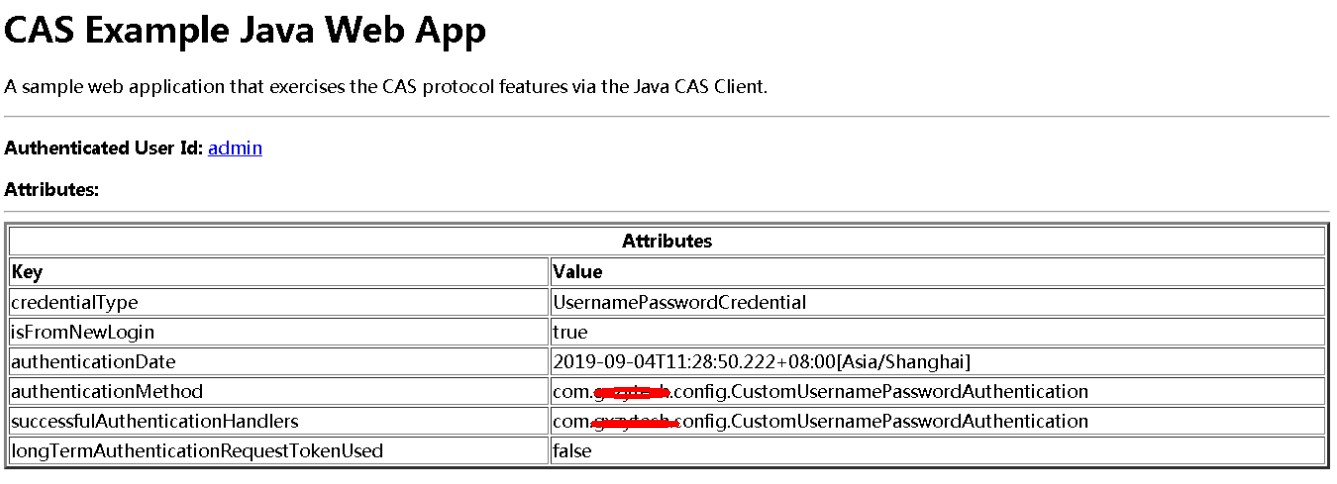
最后问题是,java客户端还是只返回了用户名
登录时控制台打印的日志如下,一开始attributes是有值的,后面不知怎么又变空了?难道是这个原因?
2019-09-04 14:46:52,558 INFO [org.apereo.inspektr.audit.support.Slf4jLoggingAuditTrailManager] - <Audit trail record BEGIN
=============================================================
WHO: audit:unknown
WHAT: [result=Service Access Granted,service=http://localhost:8282/node2/,principal=SimplePrincipal(id=admin, attributes={mobil_no=12345678111, email=123456@126, username=admin}),requiredAttributes={}]
ACTION: SERVICE_ACCESS_ENFORCEMENT_TRIGGERED
APPLICATION: CAS
WHEN: Wed Sep 04 14:46:52 CST 2019
CLIENT IP ADDRESS: 0:0:0:0:0:0:0:1
SERVER IP ADDRESS: 0:0:0:0:0:0:0:1
2019-09-04 14:46:52,569 INFO [org.apereo.cas.DefaultCentralAuthenticationService] - <Granted ticket [ST-5-GCMpvMiMoVABKskshh9TqrsSNUUlkk-PC] for service [http://localhost:8282/node2/] and principal [admin]>
2019-09-04 14:46:52,569 INFO [org.apereo.inspektr.audit.support.Slf4jLoggingAuditTrailManager] - <Audit trail record BEGIN
=============================================================
WHO: admin
WHAT: ST-5-GCMpvMiMoVABKskshh9TqrsSNUUlkk-PC for http://localhost:8282/node2/
ACTION: SERVICE_TICKET_CREATED
APPLICATION: CAS
WHEN: Wed Sep 04 14:46:52 CST 2019
CLIENT IP ADDRESS: 0:0:0:0:0:0:0:1
SERVER IP ADDRESS: 0:0:0:0:0:0:0:1
=============================================================
>
2019-09-04 14:46:52,684 INFO [org.apereo.inspektr.audit.support.Slf4jLoggingAuditTrailManager] - <Audit trail record BEGIN
=============================================================
WHO: audit:unknown
WHAT: [result=Service Access Granted,service=http://localhost:8282/node2/,principal=SimplePrincipal(id=admin, attributes={}),requiredAttributes={}]
ACTION: SERVICE_ACCESS_ENFORCEMENT_TRIGGERED
APPLICATION: CAS
WHEN: Wed Sep 04 14:46:52 CST 2019
CLIENT IP ADDRESS: 127.0.0.1
SERVER IP ADDRESS: 127.0.0.1
=============================================================