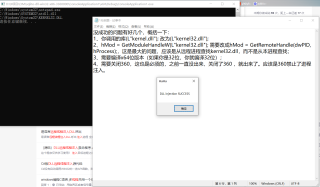
我是个初学者 最近学习Windows远程线程注入 照着书上理解了一遍 然后实现代码的时候 发现总是不成功
这个程序功能是让在用户在控制台上向程序输入两个参数 一个是notepad.exe的PID 一个是DLL路径 注入目标DLL后 出现弹窗
下面展示过程:
打开记事本
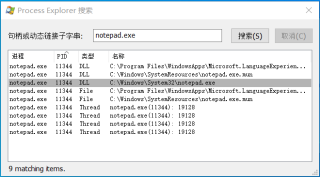
获取其PID:
打开控制台输入命令:
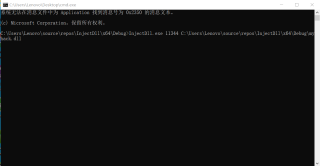
没看出什么错误:
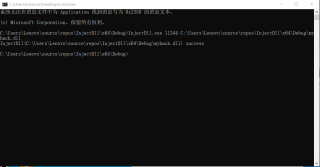
但记事本进程被关闭 没有任何效果
请问代码的问题具体在哪里?
下面是代码
//InjectDll.cpp
#include "tchar.h"
#include <windows.h>
#include <stdio.h>
BOOL InjectDll(DWORD dwPID, LPCTSTR szDllPath)
{
HANDLE hProcess = NULL, hTread = NULL;
HMODULE hMod = NULL;//DLL模块
LPVOID pRemoteBuf = NULL;//插入字符串的缓冲区
DWORD dwBufSize = (DWORD)(_tcslen(szDllPath) + 1) * sizeof(TCHAR);//DLL路径字符串大小长度
LPTHREAD_START_ROUTINE pThreadProc;//定义函数指针
//使用dwPID获取目标进程(notepad.exe)句柄
if (!(hProcess = OpenProcess(PROCESS_ALL_ACCESS, FALSE, dwPID)))
{
_tprintf(TEXT("OpenProcess(%d) failed [%d]\n"), dwPID, GetLastError());
return FALSE;
}
//在目标进程(notepad.exe)内存中分配szDllName大小的内存
pRemoteBuf = VirtualAllocEx(hProcess, NULL, dwBufSize, MEM_COMMIT, PAGE_READWRITE);
//将myhack.dll路径写入分配的内存
if (pRemoteBuf == NULL)
return FALSE;
//将DLL路径字符串写入内存地址
WriteProcessMemory(hProcess, pRemoteBuf, (LPVOID)szDllPath, dwBufSize, NULL);
//获取LoadLibraryW() API的地址
hMod = GetModuleHandleW(L"kernel.dll");
pThreadProc = (LPTHREAD_START_ROUTINE)GetProcAddress(hMod, "LoadLibraryW");
//在notepad.exe进程中运行线程
HANDLE hThread = CreateRemoteThread(
hProcess, NULL, 0, pThreadProc, pRemoteBuf, 0, NULL
);
if (hThread == NULL)
return FALSE;
WaitForSingleObject(hThread, INFINITE);
VirtualFreeEx(hProcess, pRemoteBuf, dwBufSize, MEM_FREE);
CloseHandle(hThread);
CloseHandle(hProcess);
return TRUE;
}
int _tmain(int argc, TCHAR *argv[])
{
if (argc != 3)
{
_tprintf(TEXT("USAGE :%s pid dll_path\n"), argv[0]);
return 1;
}
//inject DLL
if (InjectDll((DWORD)_tstol(argv[1]), argv[2]))
wprintf(L"InjectDll(%hs) success\n", argv[2]);
else
wprintf(L"InjectDll(%hs) failed\n", argv[2]);
return 0;
}
//myhack.cpp 会生成一个DLL文件 用来注入
#include <stdlib.h>
#include "windows.h"
#include "tchar.h"
#include <stdio.h>
HMODULE g_hMod = NULL;
DWORD WINAPI ThreadProc(LPVOID lParam)
{
MessageBox(NULL, TEXT("DLL injection SUCCESS"), TEXT("HaHa"), MB_OK);
return 0;
}
BOOL WINAPI DllMain(HINSTANCE hinstDLL, DWORD fdwReason, LPVOID lpvReserved)
{
HANDLE hThread = NULL;
g_hMod = (HMODULE)hinstDLL;
switch (fdwReason)
{
case DLL_PROCESS_ATTACH:
OutputDebugString("Myhack.dll Injection\n");//输出字符串
hThread = CreateThread(NULL, 0, ThreadProc, NULL, 0, NULL);
CloseHandle(hThread);
break;
}
return TRUE;
}