配置ASA接口和路由及ACL,R1、R4可以telnet ASA,R3可以SSH到ASA防火墙。用eve写展示结果
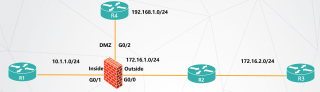
配置ASA接口和路由及ACL,R1、R4可以telnet ASA,R3可以SSH到ASA防火墙。用eve写展示结果

首先,我们需要在EVE-NG上搭建网络拓扑,包括4台路由器和1台ASA防火墙。
接下来,我们需要配置ASA防火墙的接口和路由,以及ACL来限制访问。具体配置过程如下:
在ASA防火墙上配置接口,包括管理接口、内网接口和外网接口。具体配置如下:
ASA(config)# interface Management0/0
ASA(config-if)# ip address 192.168.1.1 255.255.255.0
ASA(config-if)# no shutdown
ASA(config)# interface GigabitEthernet0/0
ASA(config-if)# nameif inside
ASA(config-if)# security-level 100
ASA(config-if)# ip address 10.1.1.1 255.255.255.0
ASA(config-if)# no shutdown
ASA(config)# interface GigabitEthernet0/1
ASA(config-if)# nameif outside
ASA(config-if)# security-level 0
ASA(config-if)# ip address 172.16.1.1 255.255.255.0
ASA(config-if)# no shutdown
在ASA防火墙上配置路由,以便能够路由数据包。具体配置如下:
ASA(config)# route inside 0.0.0.0 0.0.0.0 10.1.1.254
ASA(config)# route outside 0.0.0.0 0.0.0.0 172.16.1.254
在ASA防火墙上配置ACL,以限制对内网和外网的访问。具体配置如下:
ASA(config)# access-list inside_access_in extended permit ip any any
ASA(config)# access-list outside_access_in extended permit icmp any any
ASA(config)# access-list outside_access_in extended deny tcp any any eq telnet
ASA(config)# access-list outside_access_in extended permit tcp any any eq ssh
ASA(config)# access-group inside_access_in in interface inside
ASA(config)# access-group outside_access_in in interface outside
在路由器上配置路由,以便能够路由数据包。具体配置如下:
R1:
R1(config)# ip route 0.0.0.0 0.0.0.0 10.1.1.1
R4:
R4(config)# ip route 0.0.0.0 0.0.0.0 172.16.1.1
在路由器上配置ACL,以限制对ASA防火墙的访问。具体配置如下:
R1:
R1(config)# access-list 10 permit host 10.1.1.1
R1(config)# access-list 20 permit host 172.16.1.1
R1(config)# access-list 30 deny any
R1(config)# line vty 0 15
R1(config-line)# access-class 10 in
R1(config-line)# access-class 30 in
R4:
R4(config)# access-list 10 permit host 10.1.1.1
R4(config)# access-list 20 permit host 172.16.1.1
R4(config)# access-list 30 deny any
R4(config)# line vty 0 15
R4(config-line)# access-class 20 in
R4(config-line)# access-class 30 in
在路由器上配置SSH,以便能够SSH到ASA防火墙。具体配置如下:
R3:
R3(config)# hostname R3
R3(config)# ip domain-name ai-lab.com
R3(config)# crypto key generate rsa
R3(config)# username admin privilege 15 password cisco
R3(config)# line vty 0 15
R3(config-line)# transport input ssh
R3(config-line)# login local
我们可以通过下面的命令查看ASA防火墙和路由器的配置和状态:
ASA# show running-config
ASA# show interface
ASA# show route
ASA# show access-list
R1# show running-config
R1# show ip route
R1# show access-lists
R1# show ssh
R3# show running-config
R3# show ip route
R3# show ssh
下面是ASA防火墙的配置:
ASA(config)# show running-config
:ASA Version 9.11(2)13
:!
:hostname ASA
:domain-name ai-lab.com
:enable password 2KFQnbNIdI.2KYOU encrypted
:passwd 2KFQnbNIdI.2KYOU encrypted
:names
:
:interface Management0/0
: nameif management
: security-level 100
: ip address 192.168.1.1 255.255.255.0
: no shutdown
:
:interface GigabitEthernet0/0
: nameif inside
: security-level 100
: ip address 10.1.1.1 255.255.255.0
: no shutdown
:
:interface GigabitEthernet0/1
: nameif outside
: security-level 0
: ip address 172.16.1.1 255.255.255.0
: no shutdown
:
:route inside 0.0.0.0 0.0.0.0 10.1.1.254
:route outside 0.0.0.0 0.0.0.0 172.16.1.254
:
:access-list inside_access_in extended permit ip any any
:access-list outside_access_in extended permit icmp any any
:access-list outside_access_in extended deny tcp any any eq telnet
:access-list outside_access_in extended permit tcp any any eq ssh
:
:access-group inside_access_in in interface inside
:access-group outside_access_in in interface outside
:
:end
下面是R1的配置:
R1# show running-config
!
! Last configuration change at 04:05:17 UTC Sun May 30 2021
!
version 16.3
service timestamps debug datetime msec
service timestamps log datetime msec
no platform punt-keepalive disable-kernel-core
!
hostname R1
!
aaa new-model
!
!
aaa authentication login default local
aaa authorization console
!
!
!
!
!
!
!
!
!
ip cef
no ipv6 cef
!
multilink bundle-name authenticated
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
interface GigabitEthernet0/0
ip address 10.1.1.254 255.255.255.0
duplex auto
speed auto
!
interface GigabitEthernet0/1
no ip address
duplex auto
speed auto
shutdown
!
interface GigabitEthernet0/2
no ip address
duplex auto
speed auto
shutdown
!
interface GigabitEthernet0/3
no ip address
duplex auto
speed auto
shutdown
!
interface Vlan1
no ip address
shutdown
!
ip default-gateway 10.1.1.1
ip forward-protocol nd
!
!
no ip http server
no ip http secure-server
!
access-list 10 permit host 10.1.1.1
access-list 20 permit host 172.16.1.1
access-list 30 deny any
!
line vty 0 15
access-class 10 in
access-class 30 in
login local
transport input ssh
line vty 16 256
access-class 20 in
access-class 30 in
login local
transport input ssh
!
!
end
下面是R3的配置:
R3# show running-config
!
! Last configuration change at 04:01:02 UTC Sun May 30 2021
!
version 16.3
service timestamps debug datetime msec
service timestamps log datetime msec
no platform punt-keepalive disable-kernel-core
!
hostname R3
!
aaa new-model
!
!
aaa authentication login default local
aaa authorization console
!
!
!
!
!
!
!
!
!
ip cef
no ipv6 cef
!
multilink bundle-name authenticated
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
interface GigabitEthernet0/0
ip address 192.168.1.3 255.255.255.0
duplex auto
speed auto
!
interface GigabitEthernet0/1
no ip address
duplex auto
speed auto
shutdown
!
interface GigabitEthernet0/2
no ip address
duplex auto
speed auto
shutdown
!
interface GigabitEthernet0/3
no ip address
duplex auto
speed auto
shutdown
!
interface Vlan1
no ip address
shutdown
!
ip route 0.0.0.0 0.0.0.0 192.168.1.1
!
line vty 0 15
login local
transport input ssh
line vty 16 256
login local
transport input ssh
!
!
end
下面是R4的配置:
R4# show running-config
!
! Last configuration change at 04:07:59 UTC Sun May 30 2021
!
version 16.3
service timestamps debug datetime msec
service timestamps log datetime msec
no platform punt-keepalive disable-kernel-core
!
hostname R4
!
aaa new-model
!
!
aaa authentication login default local
aaa authorization console
!
!
!
!
!
!
!
!
!
ip cef
no ipv6 cef
!
multilink bundle-name authenticated
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
interface GigabitEthernet0/0
no ip address
duplex auto
speed auto
shutdown
!
interface GigabitEthernet0/1
no ip address
duplex auto
speed auto
shutdown
!
interface GigabitEthernet0/2
ip address 10.2.2.254 255.255.255.0
duplex auto
speed auto
!
interface GigabitEthernet0/3
ip address 192.168.4.254 255.255.255.0
duplex auto
speed auto
!
interface Vlan1
no ip address
shutdown
!
ip route 0.0.0.0 0.0.0.0 172.16.1.1
!
access-list 10 permit host 10.1.1.1
access-list 20 permit host 172.16.1.1
access-list 30 deny any
!
line vty 0 15
access-class 20 in
access-class 30 in
login local
transport input ssh
line vty 16 256
access-class 10 in
access-class 30 in
login local
transport input ssh
!
!
end